Ansible Tower / AWX provides an option to store multiple credentials in an encrypted format. It supports multiple credential types which include AWS, Google Cloud computing, Insights, Redhat CloudForms, OpenStack, Network, VMware vCenter, and Redhat Satellite. We could also add custom credential type to authenticate with other components. In the first part of the article, we will demonstrate that adding credentials to authenticate with the Linux system.
1. Login to Ansible Tower / AWX with admin privileges.
2. Navigate to credentials tab. Click on “+” to create new credentials.
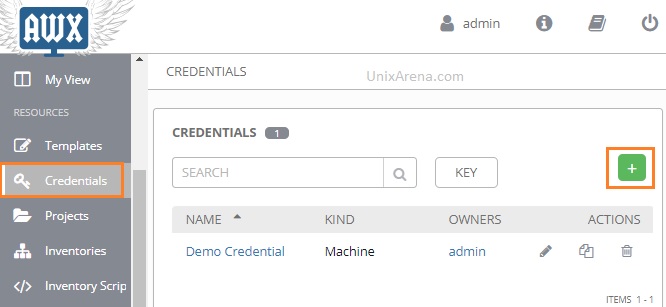
3. Enter the credential name, description, organization and search for credential type.
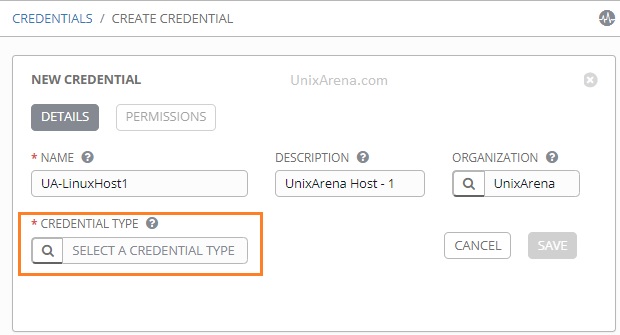
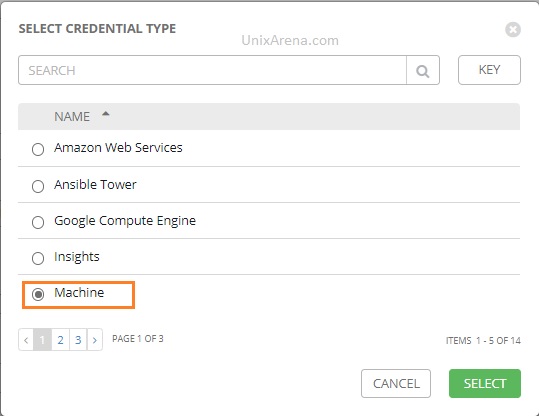
4. From the list, select “Machine” to add username and password as credentials.
5. Enter the username and password to store the credential.
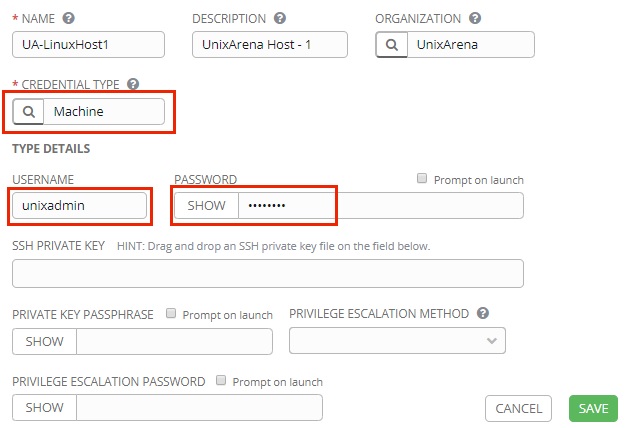
This stored credential can be added in “Template” to authenticate with inventory host. Similar way, you could authenticate with various services by selecting the right credentials type.
We might be in the situation where the need to authenticate service in which credentials type does not exist in Tower/AWX. In such a cases, we need to build a custom credential type. Credential types consist of two key concepts – “inputs” and “injectors“.
- Inputs define the value types that are used for this credential – such as a username, a password, a token, or any other identifier that’s part of the credential.
- Injectors describe how these credentials are exposed for Ansible to use – this can be Ansible extra variables, environment variables, or templated file content.
Creating the Custom Credential type in Ansible Tower/ AWX:
1. Login Ansible Tower/AWX with administrator privileges.
2. Navigate to custom credential type and click on “+” to create new.
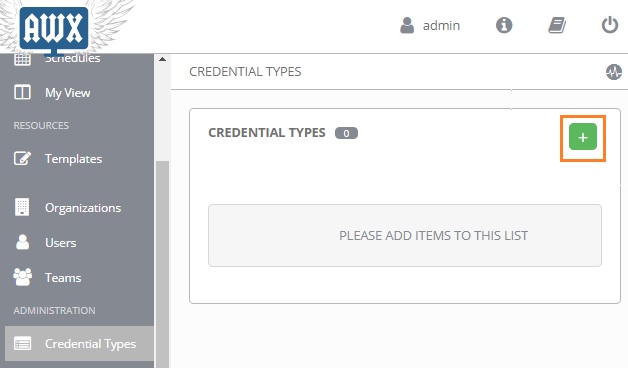
3. Update the input & inject fields with desired values. In this example, I am creating the custom credential type for Jenkins authentication.
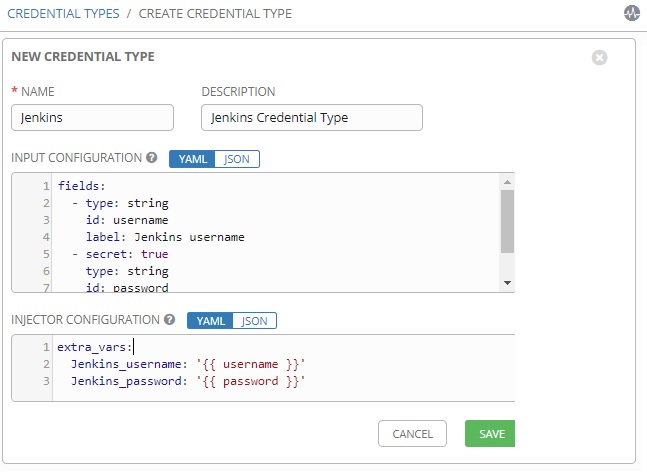
Input:
fields:
- type: string
id: username
label: Jenkins username
- type: string
id: password
label: "Jenkins password"
secret: True
required:
- username
- password
Injector:
extra_vars:
Jenkins_username: '{{ username }}'
Jenkins_password: '{{ password }}'
4. Here is the newly created credential type.
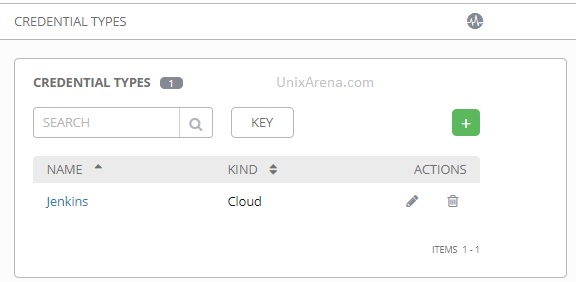
5. Navigate back to Credential. Create a new credential for Jenkins portal authentication. Click on the Credential type’s search box.
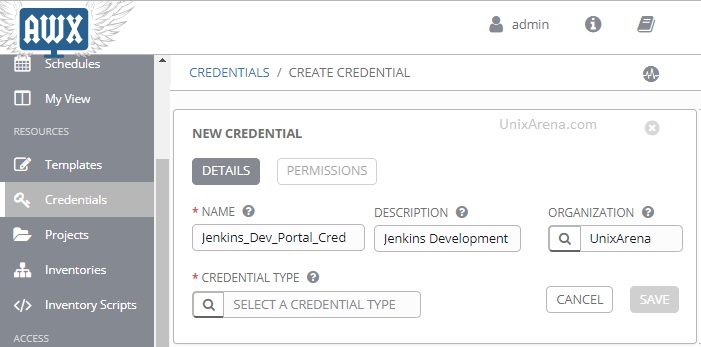
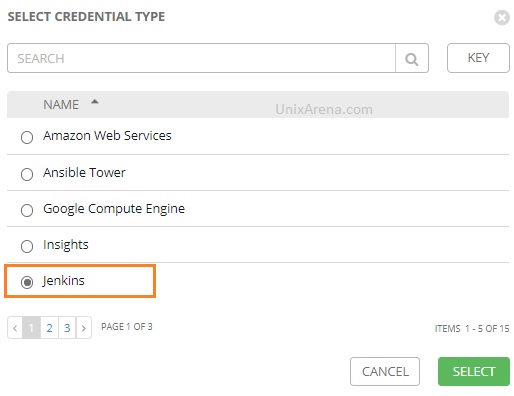
6. Select the credential type which we have created for Jenkins.
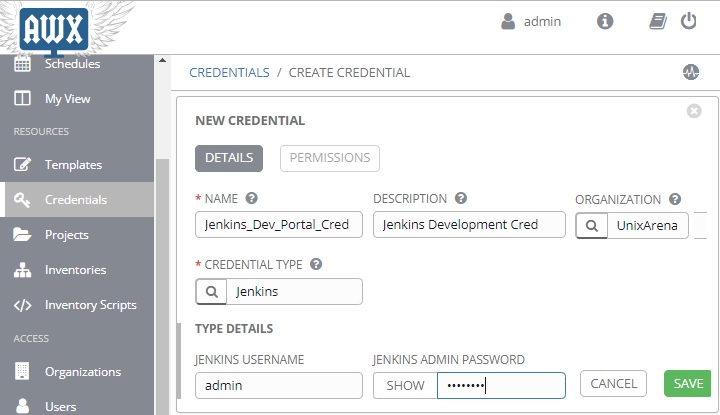
7. Enter Jenkins username & password to authenticate to the portal.
8. In your playbook, you need to call the injector’s extra-vars for successful authentication. Refer step : 3 to know the extra_vars.
Example:
- name: Create a Jenkins job creation using Ansible playbook
jenkins_job:
config: "{{ lookup('file', '/tmp/jenkinsjob.xml') }}"
name: Jenkinsdemo
user: "{{ Jenkins_username }}"
password: "{{ Jenkins_password }}"
url: http://192.168.3.142:8080
9. Add Jenkins credential in playbook template if your job requires Jenkins authentication. We have successfully created custom credential type and created new credentials using that.
Hope this article is informative to you. Share it! Comment it !! Be Sociable !!!
PRash says
Any info on how to use the pre-built credential types. For eg, I created Azure credential, but can’t find any info on how to use that in playbook.
Drake says
hi,
thanks for the article.
I tried similar to what you posted but when i try to call Jenkins_username from playbook I get error :
The task includes an option with an undefined variable. The error was: ‘Jenkins_username ‘ is undefined
FYI i did create credential using the credential type.
and the playbook entry had:
– debug: var=”{{ Jenkins_username }}”
Please let me know if it is working for you?
thanks
DR
Lingeswaran R says
Verify the custom credential’s type entries. Also, ensure that you have added new credentials and tag it in template.
extra_vars:Jenkins_username: '{{ username }}'
Jenkins_password: '{{ password }}'
Lingesh